Data Security Best Practices for Cloud Based EdTech
Types of Authentication Factors
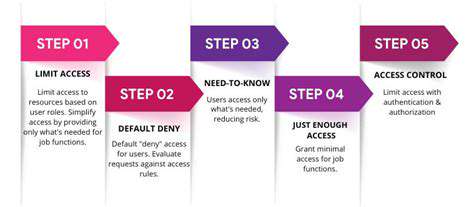
Modern authentication systems recognize three primary verification categories: knowledge factors (what you know), possession factors (what you have), and inherence factors (what you are). Knowledge factors include traditional passwords, numerical codes, or personal verification questions. Possession factors involve physical security tokens, one-time code generators, or mobile authentication applications. Inherence factors utilize unique biological characteristics such as fingerprint patterns, facial geometry, or voice characteristics. The effectiveness of any MFA system hinges on selecting an optimal combination of these methods that balances security with practicality.
Thoughtful evaluation of each factor's security properties and potential vulnerabilities is essential. While passwords remain widely used, they represent the weakest link in authentication chains. More secure MFA implementations strategically combine multiple factor types, creating formidable obstacles for would-be intruders.
Implementing MFA in Different Systems
MFA implementation strategies must be tailored to each specific technical environment. Some platforms include native MFA capabilities, while others necessitate third-party security integrations. A comprehensive implementation plan must account for the system's unique security requirements and potential vulnerability points. This planning phase should carefully assess the system's risk profile and the potential consequences of security failures.
Technical teams must possess thorough understanding of the existing infrastructure's capabilities and limitations. The deployment process typically involves authentication method configuration, user account setup, and rigorous system testing before organization-wide rollout.
Security Considerations for MFA
MFA security extends far beyond initial setup. Continuous system monitoring proves essential for identifying and addressing emerging vulnerabilities or security incidents. Periodic security evaluations and simulated attack testing help uncover system weaknesses, ensuring ongoing protection against unauthorized access attempts. This proactive maintenance approach is indispensable for preserving system integrity and safeguarding sensitive information.
Equally important is educating users about proper MFA practices. Clear, ongoing communication about MFA's security benefits and correct usage protocols helps minimize errors and maintains user vigilance. Knowledgeable users become powerful allies in maintaining organizational security, significantly strengthening overall protection.
User Experience and Usability
MFA system design significantly influences user adoption and compliance rates. Well-designed authentication flows encourage user acceptance of additional security measures, while cumbersome implementations may prompt risky workarounds. Intuitive interfaces and unambiguous guidance form the foundation of successful MFA experiences. Efficient processes and clearly worded authentication prompts dramatically improve user satisfaction.
Effective designs must accommodate diverse user capabilities and technical proficiencies. This includes providing accessible support channels for users encountering authentication difficulties.
Choosing the Right MFA Solution
Selecting an appropriate MFA solution requires careful evaluation of organizational requirements and available resources. Implementation teams must weigh factors including budgetary constraints, system growth potential, and compatibility with current infrastructure. Financial practicality and long-term operational viability should feature prominently in solution comparisons. Equally important is assessing the quality of technical support and maintenance services offered by potential providers.
Comprehensive research into vendor offerings and their respective security capabilities is imperative. Decision-makers must carefully consider how their choices will impact both immediate security posture and future operational flexibility.