Ensuring Data Transparency in Mobile Learning Solutions
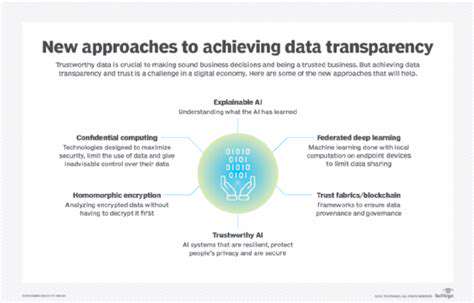
Defining and Implementing Data Transparency Protocols

Defining Data Transformation
Data transformation represents a fundamental phase in analytical processes, involving diverse activities that reshape or enhance information to meet specific analytical needs. This multifaceted procedure typically includes format conversion, data cleansing, information aggregation, and creation of new variables. Grasping the analysis's unique demands proves critical when determining which transformations to apply. For sales trend analysis, transformations might involve compiling daily figures into monthly summaries and computing growth percentages. Thoughtful planning helps prevent distortions in final outcomes.
An essential component involves mapping data pathways - identifying source locations, original formats, and required fields. Precisely outlining these elements aligns the transformation workflow with project goals while preventing avoidable complications. This stage also requires documenting specific procedures like cleaning methods, computational steps, and manipulation techniques.
Implementing Data Transformation Strategies
Execution of transformation approaches spans from basic cleansing to sophisticated modeling. Cleaning procedures address missing values, inconsistencies, and duplicate entries - all vital for ensuring information quality that underpins reliable analysis. Thorough attention to data integrity issues forms the foundation for credible analytical results. Practical examples include standardizing date formats or managing statistical outliers during cleaning phases.
Tool selection significantly impacts transformation implementation. Different platforms suit varying data types and volumes - SQL for database operations versus Python/R for complex manipulations. Choosing appropriate technologies guarantees both efficiency and precision in data handling. Equally important is establishing verification protocols to confirm expected outputs and maintain data integrity through validation testing against predefined benchmarks.
Choosing the Right Data Transformation Techniques
Technique selection profoundly influences analytical accuracy and relevance. Decisions should consider both data characteristics and research objectives. Customer behavior analysis might require segmentation by demographic or purchase history. Proper technique application ensures transformations accurately reveal underlying patterns and relationships. Evaluation should include comparing normalization, standardization, and aggregation methods to identify optimal approaches.
Assessing potential biases and constraints proves essential when selecting methodologies. Methods should preserve original data patterns without introducing artifacts. Practical considerations like computational resources also factor into decisions, as some transformations demand significant processing power. Comprehensive planning and testing verify technique suitability for specific datasets and analytical goals.
Documentation ensures reproducibility and maintenance efficiency. Records should detail procedural steps, decision rationales, and expected outputs. Maintaining clear transformation trails enables analysis replication and safeguards data integrity. Such documentation facilitates understanding among different analysts working with the same datasets.
Accountability and Compliance with Regulations
Defining Accountability
Mobile application data accountability transcends regulatory compliance, requiring proactive transparency about collection methods, usage purposes, and protection measures. Developers must provide accessible privacy policies detailing specific data types, their applications, and security safeguards. Understanding potential breach consequences enables prompt, effective responses when issues emerge.
Accountability further demands continuous monitoring of data practices. Routine evaluations identify vulnerabilities while verifying policy effectiveness in privacy protection. This vigilant approach builds user trust and demonstrates authentic commitment to responsible data stewardship, strengthening company-user relationships.
Compliance with Data Privacy Regulations
Alignment with GDPR, CCPA, and similar frameworks remains crucial for mobile app accountability. These regulations define permissible data collection scopes, usage parameters, and user rights. Compliance requires thorough understanding of legal requirements and their practical implications. Non-compliance risks severe penalties and reputational damage.
Establishing efficient systems for data subject requests (access/deletion) constitutes another compliance cornerstone. Streamlined procedures demonstrate respect for user rights while ensuring regulatory adherence. Staff training on data handling responsibilities and legal obligations maintains organizational compliance awareness.
Transparency in Data Handling Practices
Clear communication about data practices fosters user confidence. Disclosures should explain collection methods, utilization purposes, and protection mechanisms, including third-party data sharing arrangements.
Privacy policies and terms of service require plain language formulations. Overly complex documentation creates comprehension barriers, undermining transparency. User-friendly formats like simplified summaries and interactive explainers significantly enhance understanding and trust.
Security Measures and Data Protection
Comprehensive security protocols form the backbone of accountable data practices, incorporating both technical safeguards (encryption, access controls) and breach response procedures. Timely user notification mitigates security incident impacts, while regular audits proactively identify system vulnerabilities.
Data minimization principles further enhance protection by limiting collection to essential information and implementing secure disposal protocols. Following storage/transmission best practices, combined with user security education, collectively strengthen accountability and trust.
Read more about Ensuring Data Transparency in Mobile Learning Solutions
Hot Recommendations
- Attribution Modeling in Google Analytics: Credit Where It's Due
- Understanding Statistical Significance in A/B Testing
- Future Proofing Your Brand in the Digital Landscape
- Measuring CTV Ad Performance: Key Metrics
- Negative Keywords: Preventing Wasted Ad Spend
- Building Local Citations: Essential for Local SEO
- Responsive Design for Mobile Devices: A Practical Guide
- Mobile First Web Design: Ensuring a Seamless User Experience
- Understanding Your Competitors' Digital Marketing Strategies
- Google Display Network: Reaching a Broader Audience